Building Situational Awareness Through Three Types of Security Data
In the evolving corporate security world, situational awareness is no longer a "nice-to-have” it’s a crucial part of protecting people, assets, and operations. Today’s leading corporate security teams know that making the right decision at the right time requires a multi-layered approach to data. In this post, we’ll discuss the four essential layers of security data that can enhance situational awareness and improve security outcomes.
Layer 1: Internal Incident Data
The innermost layer of security data is your company’s internal incident data. This is the firsthand information gathered from incidents that directly impact your organization, such as a break-in at a warehouse, a robbery at a retail location, or an executive's security breach while traveling abroad. These incidents are documented in a repository such as an incident management tool, capturing key details about what happened, where it occurred, the timing, and the company’s response. This data is uniquely specific to your organization, offering valuable insight into patterns of threats and risks that are directly relevant to your operational landscape. By closely analyzing this layer, security teams can improve their response strategies and gain a clearer picture of recurring risks.
Layer 2: Historical Crime and Unrest Data
The second layer includes historical crime and unrest data around relevant company locations. This is external data that isn’t specific to your organization but provides insights into crime patterns near your business assets. For instance, a retailer would benefit from data on the frequency of thefts in neighborhoods surrounding its stores, while a manufacturing company would monitor crime levels near its warehouses. Although this data is widely available, it often comes from fragmented sources, making it challenging for security teams to consolidate and analyze without a platform like Base Operations. With tools that ingest, normalize, and analyze this data, security teams can gain a much-needed perspective on external threats that could impact their operations, helping them make proactive security decisions.
Layer 3: External Contextual Data
The third layer consists of external data that doesn’t directly pertain to crime or unrest but has a tangential impact on security risks. For example, weather patterns can influence crime trends—high temperatures in the summer may correlate with increased crime levels in certain areas. Similarly, geopolitical events, such as significant elections or policy shifts, can drive fluctuations in unrest. Even events like sports games can create ripple effects in local crime levels, especially if tensions run high among fans. By incorporating contextual data like weather, political events, or large gatherings, security teams can add predictive layers to their analysis, preparing for surges in security incidents that may not be immediately apparent.
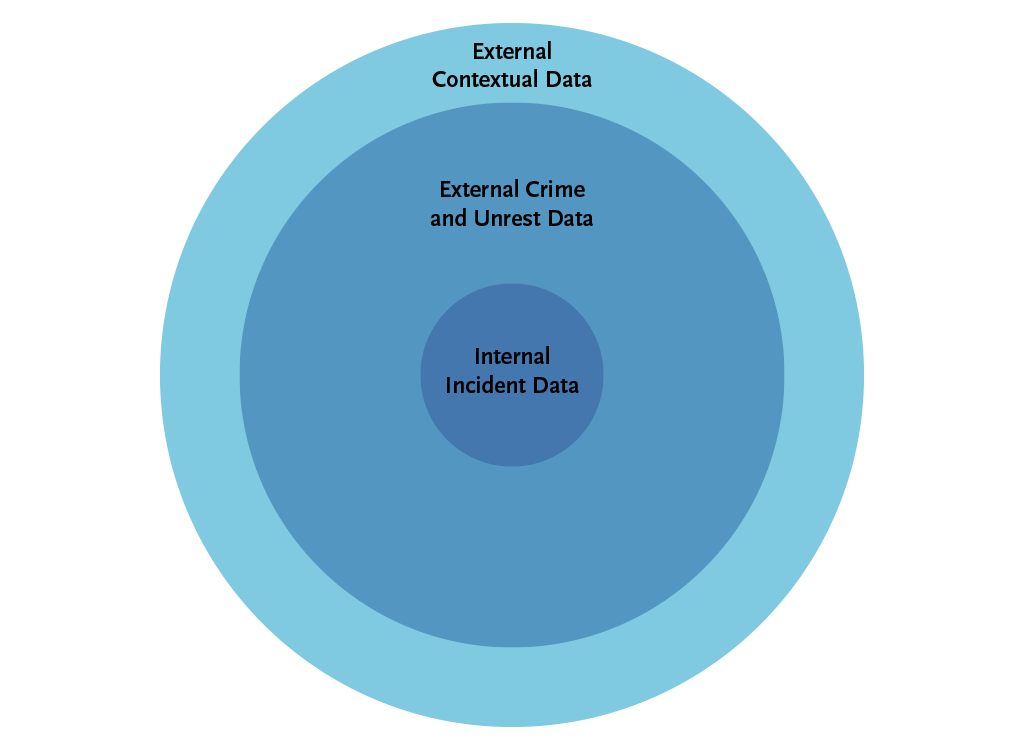
Expanding Situational Awareness with a Multi-Layered Approach
By layering these four types of data—internal incident data, historical crime and unrest data, external contextual data, and real-time threat intelligence—corporate security teams can achieve a comprehensive situational analysis. This multi-layered approach transforms data into actionable insights, empowering teams to move from reactive responses to proactive risk management. Industry-leading security teams understand the value of integrating these data layers to anticipate potential risks and optimize resource allocation.
With a cohesive view of what’s happening both inside and outside the organization, security teams can make informed, strategic decisions that safeguard their employees, assets, and operations. By using these four layers of data in combination, corporate security teams are enhancing their situational awareness and moving one step closer to a world where security risks are managed with both precision and foresight.
Takeaways
Join 1100+ security leaders getting new ideas on how to better protect their people and assets.